
- Home
- About Us
- IT Services
- Managed IT Services
- Security Services
- Cybersecurity
- Cybersecurity Overview
- Network Security
- Business Security
- Unified Threat Management
- Endpoint Security Solutions
- Asset Tracking
- Mobile Device Management
- Email Encryption
- Multi-Factor Authentication
- Spam Protection
- Content Filtering
- Phishing Simulation
- Dark Web Monitoring
- Penetration Testing
- Compliance Standards
- Cloud Computing Services
- Industry Specific
- Data Services
- Hardware Services
- Software Services
- Business Communication
- Understanding IT
- News
- Blog
- Support
- Contact Us
- (217) 428-6449
- Register
- Login
Network Solutions Unlimited Blog
Tip of the Week: Mastering Page Orientation in Microsoft Word
There are times when using Microsoft Word that will require the addition of an outside element, usually something like an Excel sheet, PowerPoint slide or other visual aid. A common issue faced by users is having to significantly alter the size of the external element to fit between the margins of the portrait orientation, ultimately detracting from its impact.
Here is a quick example of an occasion where changing the orientation for a single page in a document might be of value.

Begin by navigating to the page inside your Microsoft Word document that you would like to change the orientation of. Once there, make sure that your cursor is on the page.
Open the Layout menu and click the button to expand the Page Setup submenu, as seen below.
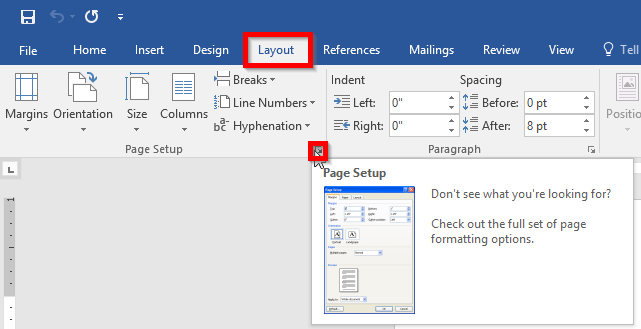
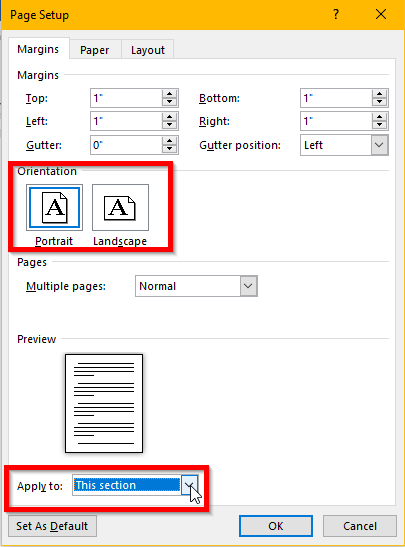
Next select the orientation you desire and select what you’d like it applied to using the drop down menu, as demonstrated. In this case, you’ll select ‘This section’. Click OK.
Looking for more tips, tricks and hints that will improve the way you and your employees make use of technology? Make sure you check back to Network Solutions Unlimited’s blog every week for the latest and greatest IT how-tos!
About the author
Frank Saulsbery began a career in technology 1998 ago after studying microelectronics in college, he now owns two technology companies, sits on several advisory boards and is requested to speak regularly on cyber security awareness and digital business protection.
Latest News & Events
Account Login
Contact Us
Learn more about what Network Solutions Unlimited can do for your business.
(217) 428-6449
3090 N Main St
Decatur, Illinois 62526

Comments