
- Home
- About Us
- IT Services
- Managed IT Services
- Security Services
- Cybersecurity
- Cybersecurity Overview
- Network Security
- Business Security
- Unified Threat Management
- Endpoint Security Solutions
- Asset Tracking
- Mobile Device Management
- Email Encryption
- Multi-Factor Authentication
- Spam Protection
- Content Filtering
- Phishing Simulation
- Dark Web Monitoring
- Penetration Testing
- Compliance Standards
- Cloud Computing Services
- Industry Specific
- Data Services
- Hardware Services
- Software Services
- Business Communication
- Understanding IT
- News
- Blog
- Support
- Contact Us
- (217) 428-6449
- Register
- Login
Network Solutions Unlimited Blog
Tip of the Week: Hey Cortana! Don’t Listen to Them, You’re my Virtual Assistant
Cortana, Windows 10’s built-in personal assistant, has proven to be useful for those users who have taken advantage of her services. Sometimes, however, the Cortana interface will answer when another person in the room beckons her. For Cortana to work for one person, and to obey only one voice, the software needs to get to know that voice.
To begin to set this up you have to open Cortana’s Settings. To do this, click on the Cortana Icon on the taskbar.

Then select the gear-shaped icon in the Cortana window to access Cortana’s settings.
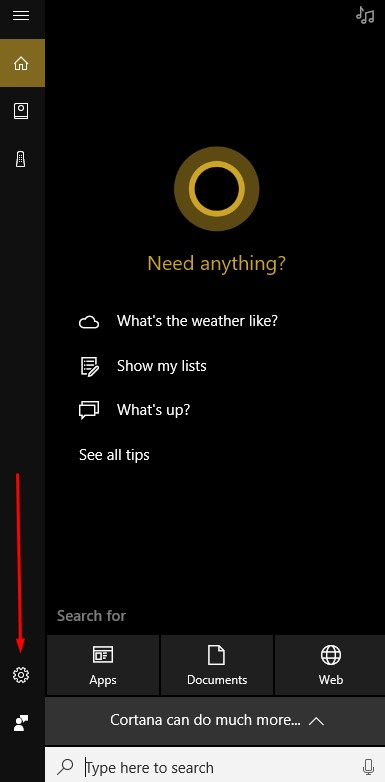
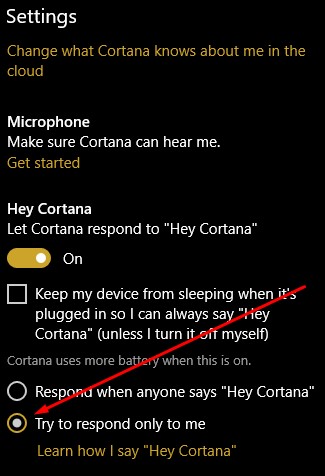
Make sure that the Let Cortana respond to “Hey Cortana” setting is toggled on.
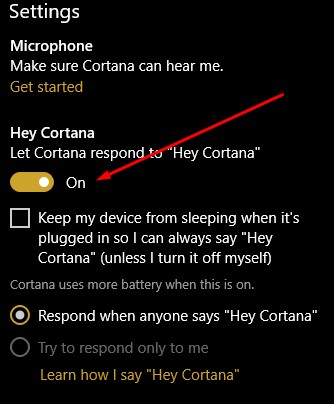
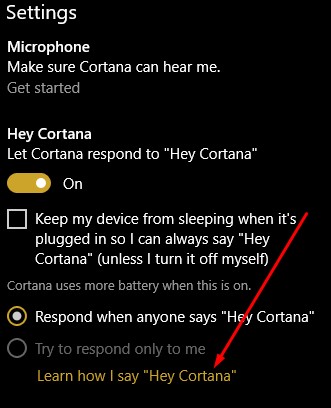
Then select Learn how I say “Hey Cortana”.
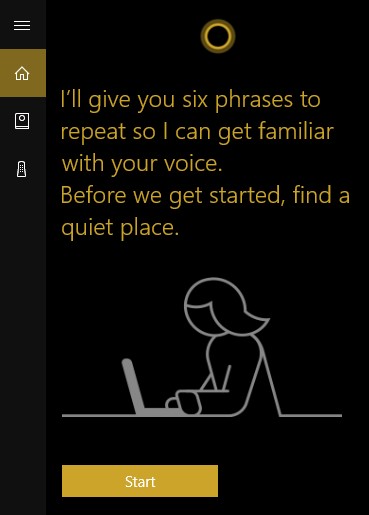
You will then be asked to answer six phrases to help Cortana determine the way you say “Hey Cortana”.
Once you’ve completed that step, return to Cortana’s settings and make sure that the try to respond only to me option is selected.
Now you have Cortana’s full attention. You can have her help you with any number of issues, while helping you navigate Windows 10.
Do you use Cortana? Siri? Google Assistant? Alexa? Bixby? If so, which are your favorites? Leave your thoughts with us in the comments below.
About the author
Frank Saulsbery began a career in technology 1998 ago after studying microelectronics in college, he now owns two technology companies, sits on several advisory boards and is requested to speak regularly on cyber security awareness and digital business protection.
Latest News & Events
Account Login
Contact Us
Learn more about what Network Solutions Unlimited can do for your business.
(217) 428-6449
3090 N Main St
Decatur, Illinois 62526

Comments